Securing your code with the XSS Sanitizer Library
XSS Sanitizer
Now that you know what XSS is and why it’s dangerous, let’s look at a powerful tool to fight it: the XSS Sanitizer.
- Step 1: What is the XSS Sanitizer?
- It’s a lightweight library you can add to any DataFlex project. Its job?
- Sanitize any string — usually user input — before storing it or showing it to other users. That way, you keep your app safe from sneaky scripts.
- Step 2: Getting started — add the library to your workspace
- You have two easy options:
- Use Maintain Libraries in the Studio to add the sanitizer
- Or just copy the sanitizer files directly into your workspace
- Step 3: What’s inside?
- The library contains a single class: cXssSanitizer — this handles all the sanitation magic.
- We’ve also created a default implementation in the package oXssSanitizerStandard.pkg, which covers over 99% of common XSS cases.
- Plus, it exposes a handy global sanitizer handle g_hO_Sanitizer for easy access.
- Step 4: How to use it?
- After you include the sanitizer package with a use statement, the main function you’ll need is:
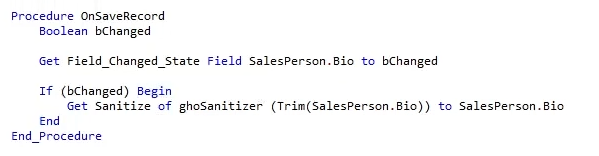
- Parse takes your dirty (unsafe) input string, removes any malicious code, tags, and attributes, and returns a clean, safe string.
- You can call Parse anywhere — before saving user input to the database, or before displaying data back to users.
- Step 5: Customize the sanitizer (optional)
- The sanitizer can be tweaked to fit your needs:
- Sanitize modes:
- sanitize_mode_allowed — Only allows tags and attributes in the allowed lists
- sanitize_mode_blocked — Blocks everything listed in the forbidden lists
- Lists you can configure:
- pasAllowedTags and pasAllowedAttributes
- pasForbiddenTags and pasForbiddenAttributes
- pasVoidTags (self-closing tags like <br>)
- You can set these lists as arrays or simply use a comma-separated string with helper procedures like SetAllowedTags.
- The default setup in oXssSanitizerStandard.pkg is solid for most projects, but feel free to customize!
- Quick recap
- We learned what XSS is and the risks it poses
- We introduced the XSS Sanitizer, a simple but powerful tool to keep your app safe
- You add the sanitizer to your project, call Parse on user input, and optionally customize its behavior
- And remember: never trust user input!
